Riverbed Steelhead Management Console (GUI)
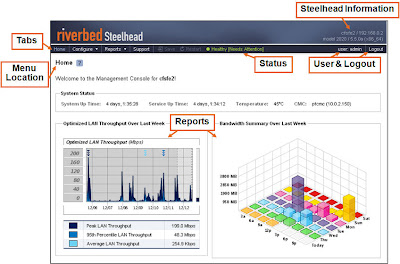
Home Page § Enter the URL for the Management Console in the location box of your Web browser: • http://host.domain or https://host.domain § Logging in • In the Account (Username) text box, type admin • In the Password text box, type the password you were assigned (default is password) • Click Log In button to display the Home page § Console requirements • The Management Console has been tested with Mozilla Firefox version 1.5.x and 2.0, and Microsoft Internet Explorer version 6.x and 7.0 • Note: JavaScript and cookies must be enabled in your Web browser • Note: If you want to encrypt your communication, you must have an SSL capable browser